If there’s something that has grow to be transparent over the last yr, it’s that Apple devices don’t seem to be as safe as the corporate needs you to consider.
We’re 4 months into 2025 and there have already been over 10 cases wherein attackers particularly centered Apple customers, and those are simply the incidents we all know of.
I’ll admit no tool is foolproof, however there appears to be a rising development the place unhealthy actors choose concentrated on Apple customers over different platforms. In reality, security researchers have just lately recognized a brand new phishing marketing campaign wherein hackers, who in the past involved in Home windows, are actually surroundings their attractions on Apple IDs.

An individual operating on an Apple pc (Kurt “CyberGuy” Knutsson)
What you want to understand
Safety researchers at LayerX Labs have exposed a brand new phishing marketing campaign that particularly goals Mac customers, marking a shift from its earlier center of attention on Home windows. The attackers first of all lured Home windows customers with faux Microsoft safety indicators designed to scouse borrow login credentials. On the other hand, after Microsoft, Chrome and Firefox carried out new safety features to dam those assaults, the hackers began redirecting their efforts towards Mac customers as an alternative.
The brand new assault intently mirrors its predecessor however with key changes. The phishing pages were redesigned to resemble Apple’s safety warnings, making them seem professional to macOS users. The assault code has additionally been adjusted to particularly come across macOS and Safari customers, making sure that handiest Apple customers see the fraudulent pages.
Plus, regardless of transferring their center of attention, the attackers proceed to host those phishing pages on Microsoft’s Home windows[.]internet area. Since it is a depended on Microsoft platform, it permits the phishing pages to evade detection by way of safety gear that assess chance in keeping with area recognition.
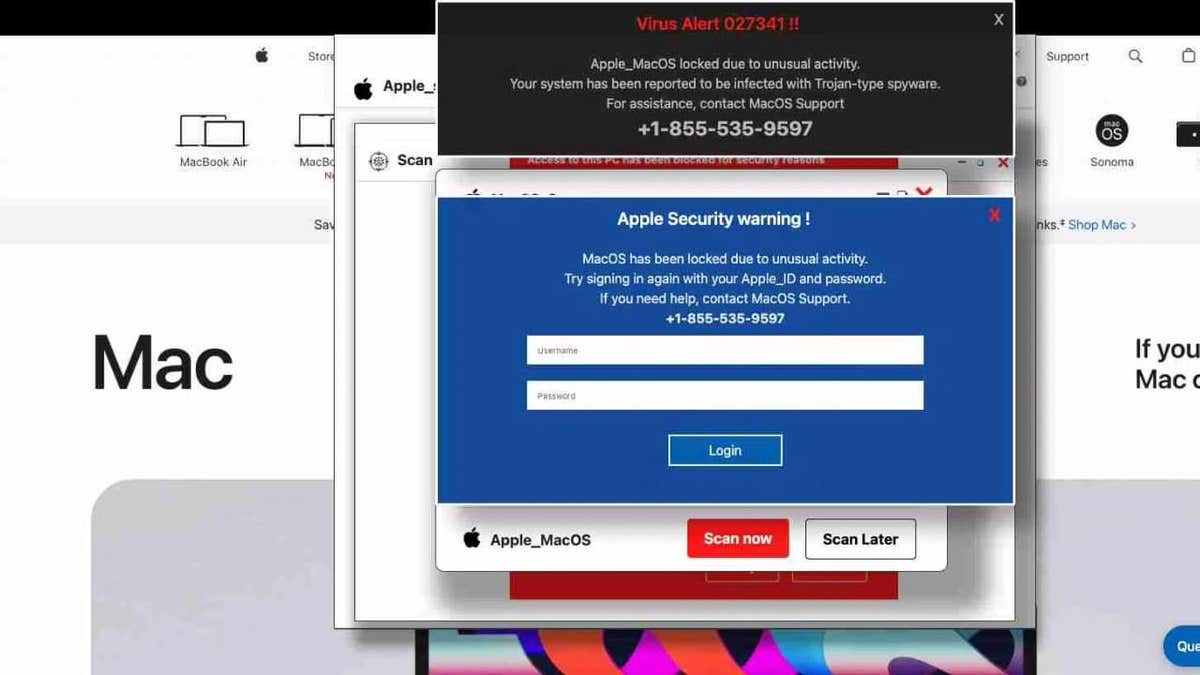
Compromised internet sites exhibiting faux safety caution (LayerX)
FBI WARNS OF DANGEROUS NEW ‘SMISHING’ SCAM TARGETING YOUR PHONE
How sufferers are lured in
The phishing marketing campaign exploits not unusual but extremely efficient strategies referred to as typosquatting and malicious redirects. Sufferers steadily finally end up on those phishing pages after creating a easy mistake, corresponding to mistyping a URL whilst looking to consult with a sound web site.
As an alternative of achieving the meant website, they land on a compromised area parking web page. From there, they’re redirected thru a couple of internet sites sooner than in the long run arriving on the phishing web page, which gifts a faux Apple safety caution. Believing their Apple ID is in peril, sufferers are tricked into coming into their credentials, unknowingly handing them over to the attackers.
One notable case concerned an individual the usage of Safari who was once operating at a industry secured by way of a Safe Internet Gateway. In spite of the group’s security features, the phishing strive controlled to avoid the gateway’s protections.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
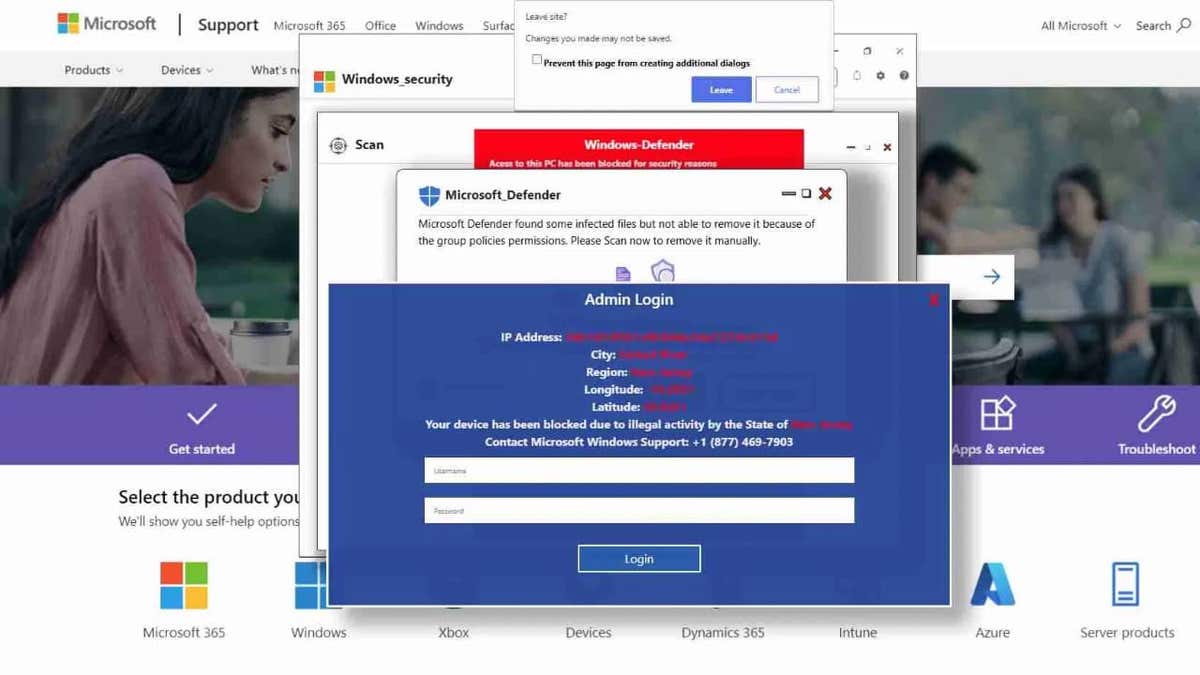
Compromised internet sites exhibiting faux safety caution (LayerX)
APPLE’S IOS VULNERABILITY EXPOSES IPHONES TO STEALTHY HACKER ATTACKS
7 tactics to stick protected from attackers concentrated on Apple customers
Phishing campaigns are more and more concentrated on macOS customers, however you’re no longer defenseless. Listed below are 4 very important steps to offer protection to your self.
1. Use sturdy antivirus instrument: A competent antivirus program is your first defensive line towards phishing makes an attempt and malicious internet sites. Whilst Apple’s integrated safety features supply some coverage, they aren’t foolproof, particularly towards subtle phishing assaults that mimic professional Apple warnings. A powerful antivirus resolution can come across and block malicious websites sooner than you even succeed in them, fighting you from unintentionally coming into your credentials on a fraudulent web page. Moreover, complicated safety instrument can determine suspicious redirects and provide you with a warning sooner than you fall sufferer to typosquatting traps. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
2. Stay your instrument up to the moment: Common updates to macOS and your applications aren’t as regards to new options. They’re vital patches that repair safety vulnerabilities. Attackers are fast to milk any weak point, so making sure your running gadget and all put in instrument are present minimizes the chance of a breach. Allow computerized updates the place conceivable so that you’re all the time secure by way of the most recent safety improvements.
3. Incessantly observe your Apple ID process: Even with sturdy security features in position, it’s necessary to control your Apple ID account for any indicators of unauthorized get right of entry to. Apple permits customers to study their account process, together with units logged into the account and up to date adjustments. Incessantly take a look at your Apple ID settings to be sure that handiest depended on units are attached and that no suspicious process has came about. If you happen to realize anything else extraordinary, corresponding to login makes an attempt from unfamiliar places, in an instant trade your password and take away unauthorized units. This proactive manner permit you to catch possible breaches early and decrease harm.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
4. Allow two-factor authentication (2FA): Sturdy, distinctive passwords for each and every account are very important, however they’re much more efficient when mixed with two-factor authentication. Despite the fact that attackers arrange to scouse borrow your credentials thru a phishing assault, 2FA provides an additional barrier that makes unauthorized get right of entry to considerably tougher. Imagine the usage of a password manager to generate and retailer complicated passwords. Get extra information about my best expert-reviewed password managers of 2025 here.
5. Use a restoration key for enhanced safety: Apple gives an non-compulsory function referred to as a restoration key, which is a 28-character code that gives an additional layer of safety on your Apple ID. While you allow a restoration key, Apple disables its same old account restoration procedure, which means you’ll want this key, at the side of get right of entry to to a depended on tool or telephone quantity, to reset your password or regain get right of entry to for your account. This makes it considerably tougher for attackers to take keep watch over of your account.
To arrange a restoration key, cross to Settings > [Your Name] > Signal-in & Safety > Restoration Key for your iPhone, iPad or Mac. Observe the activates to generate and ensure your restoration key. Make sure you write it down and retailer it in a safe location, corresponding to a protected or with a depended on circle of relatives member. Needless to say shedding each your restoration key and get right of entry to to depended on units can completely lock you from your account. On the other hand, if used responsibly, this selection provides you with higher keep watch over over your account’s safety.
6. Allow biometric authentication: Apple units be offering complicated biometric authentication options like Face ID and Touch ID, which offer an additional layer of safety. Those options make it considerably tougher for attackers to achieve get right of entry to for your tool or delicate accounts, even though they arrange to scouse borrow your credentials. Allow biometric authentication anyplace conceivable, particularly for apps and services and products that retailer private or monetary knowledge. Since biometric knowledge is exclusive to you, it provides a degree of coverage that passwords by myself can’t supply.
7. Follow protected surfing: Many assaults depend on easy consumer errors, corresponding to mistyping a URL or clicking on suspicious hyperlinks. At all times test that you simply’re visiting professional internet sites sooner than coming into any private knowledge. Be skeptical of surprising safety indicators, even though they mimic Apple’s design. Studying to spot the sophisticated indicators of phishing, like extraordinary URL buildings or generic greetings, permit you to steer clear of falling for those scams.
HOW TO PROTECT YOUR IPHONE & IPAD FROM MALWARE
Kurt’s key takeaways
Apple has lengthy bought the concept its ecosystem is inherently more secure than the choices, however that declare is beginning to put on skinny. The truth is that attackers are now not ignoring Mac customers, they’re actively concentrated on them, and Apple’s reaction has been anything else however proactive. Whilst Microsoft, Google and others roll out new security features to counter evolving threats, Apple stays gradual to evolve, depending on out of date assumptions about its platform’s protection.
CLICK HERE TO GET THE FOX NEWS APP
Do you consider Apple will have to be extra clear about safety vulnerabilities affecting its customers? Tell us by way of writing us at Cyberguy.com/Contact.
For extra of my tech pointers and safety indicators, subscribe to my unfastened CyberGuy Record Publication by way of heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Observe Kurt on his social channels:
Solutions to the most-asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.



