Phishing assaults are far and wide, and maximum people can spot the most obvious ones. Even supposing any person falls for one and fingers over their password, two-factor authentication (2FA) in most cases provides a the most important layer of coverage. However a brand new phishing equipment making the rounds can bypass 2FA solely via the usage of consultation hijacking and real-time credential interception.
Referred to as Astaroth, this software intercepts and manipulates site visitors between your instrument and bonafide authentication products and services like Gmail, Yahoo and Microsoft. Because it grabs the entirety in genuine time, it utterly bypasses 2FA and offers attackers complete get admission to in your account.

Representation of a hacker at paintings (Kurt “CyberGuy” Knutsson)
How Astaroth works
Astaroth is a next-level phishing equipment that takes scamming to an entire new point. As an alternative of the usage of elementary faux login pages like conventional phishing kits, it really works as a intermediary between your instrument and the actual authentication carrier whilst silently grabbing the entirety had to smash in.
The assault starts whilst you click on on a phishing hyperlink and land on a malicious web site that appears just like the actual one. For the reason that web site has legitimate SSL certificate, there aren’t any purple flags, no safety warnings and no sketchy pop-ups. While you input your login main points, together with username, password, instrument information and IP cope with, Astaroth snatches them up earlier than passing the request to the true web site.
Two-factor authentication isn’t an issue for Astaroth. It intercepts one-time passwords the second one they’re entered, whether or not they come from an authenticator app, SMS or a push notification. The stolen codes are in an instant despatched to the attacker thru a internet panel or Telegram alert, so they may be able to use them earlier than they expire.
The true kicker is that Astaroth additionally grabs consultation cookies, which can be the small bits of knowledge that stay customers logged in after authentication. Attackers can inject those cookies into their very own browsers, skipping the will for passwords or two-factor authentication altogether. As soon as they have got the consultation, they’re in with out a further steps required.
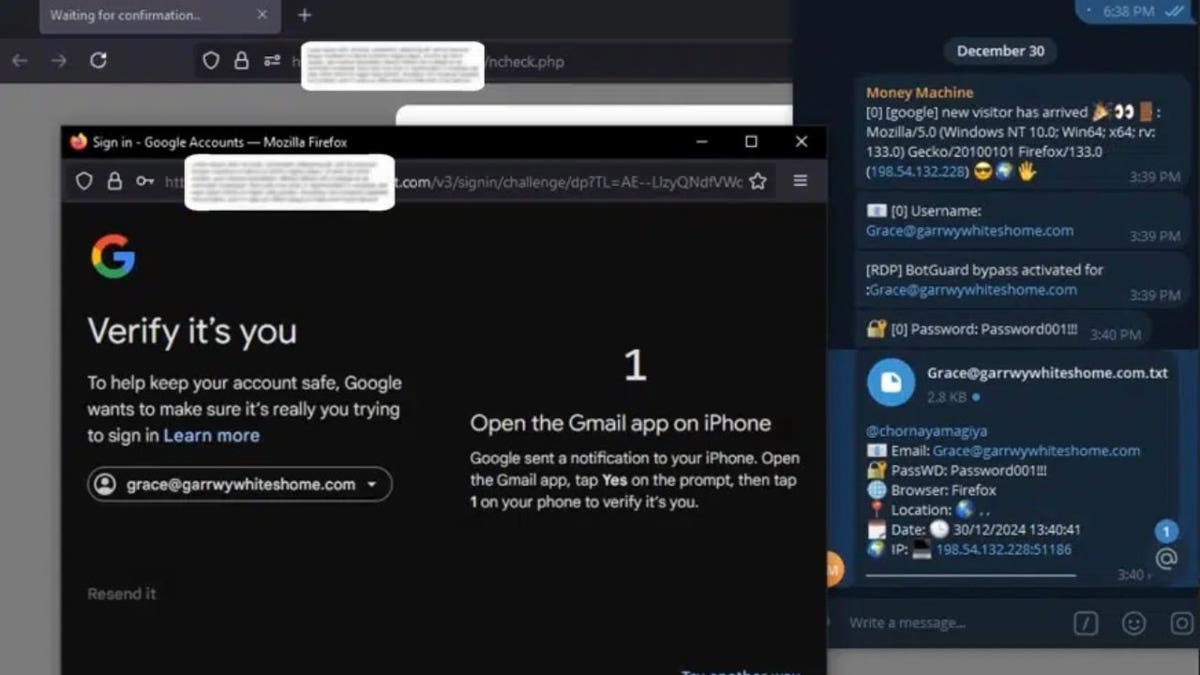
An instance of what the sufferer and attacker would see (SlashNext) (Kurt “CyberGuy” Knutsson)
BEST ANTIVIRUS FOR MAC, PC, IPHONES AND ANDROIDS – CYBERGUY PICKS
Astaroth is shockingly complicated
As reported via cybersecurity corporate SlashNext, Astaroth sticks out from different phishing kits as a result of its skill to intercept credentials in genuine time, automate assaults and face up to takedown efforts. Conventional phishing is determined by tricking sufferers into getting into their credentials on faux login pages, however Astaroth eliminates that step solely.
Past its complicated features, Astaroth comes with options that make it interesting to cybercriminals. It makes use of bulletproof internet hosting to stick on-line regardless of legislation enforcement efforts, receives common updates to avoid safety patches and follows a structured fee fashion. For $2,000, patrons get six months of constant upgrades. To construct agree with, the creators even let hackers check the phishing equipment earlier than buying.
Astaroth is broadly to be had thru Telegram and underground cybercrime boards. The anonymity of those platforms makes it tough for government to trace distribution.
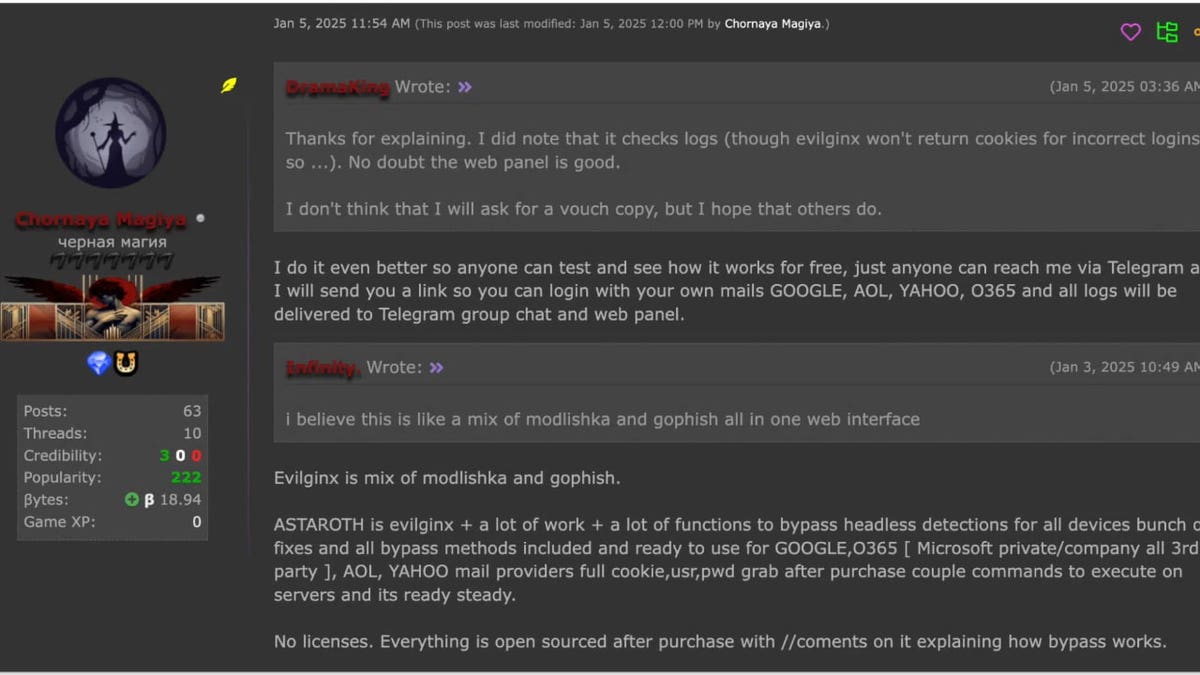
The vendor sharing data on trying out the phishing equipment out (SlashNext) (Kurt “CyberGuy” Knutsson)
HOW TO PROTECT YOUR DATA FROM IRS SCAMMERS THIS TAX SEASON
Indicators you can be inflamed with Astaroth
1) Sudden account logins or safety signals
- You obtain signals from Gmail, Microsoft or different products and services a few login from an unknown instrument or location
- You get a 2FA request whilst you weren’t looking to log in
2) You’re mysteriously logged out of accounts
- In case your consultation cookies have been stolen, an attacker may log in as you and power a log-out somewhere else
3) Password adjustments or settings updates you didn’t make
- If an attacker has keep an eye on, they’ll alternate restoration emails, telephone numbers or passwords
4) Gradual gadget efficiency or atypical habits
- Astaroth makes use of reliable Home windows processes (like WMIC, BITSAdmin or Regsvr32) to cover itself
- In case your gadget is gradual or the Job Supervisor displays unusual processes the usage of prime CPU/community with out a clarification, which may be a clue
5) Browser performing unusually
- Login fields autopopulate incorrectly or redirect loops happen
- Pages that used to paintings abruptly cause warnings or mistakes
6) Unfamiliar techniques or scripts operating within the background
- Test for atypical Scheduled Duties, Registry adjustments or background community connections (particularly if they are outbound to suspicious domain names or IPs).
What to do if you happen to suspect an infection
- Disconnect from the web right away
- Run a complete malware scan the usage of trusted antivirus device
- Test for unauthorized logins for your primary accounts and alternate all passwords on any other relied on instrument
- Permit passkeys or {hardware} safety keys the place conceivable
- Reset your instrument if malware persists; a complete manufacturing facility reset could also be required
- Track financial institution accounts and e mail inboxes for suspicious task
4 techniques to stick protected from Astaroth phishing assaults
1) Keep away from unknown hyperlinks and use robust antivirus device: Keep in mind that regardless of how complicated the malware is, it nonetheless wishes enter from you. Most often, an attacker would require you to click on a hyperlink earlier than they may be able to scouse borrow your information. As an example, for Astaroth to paintings, it’s a must to click on a hyperlink, discuss with a malicious web site and input your credentials. When you don’t click on the hyperlink, you keep transparent of the malware.
The easiest way to safeguard your self from malicious hyperlinks that set up malware, probably gaining access to your non-public data, is to have robust antivirus device put in on your whole gadgets. This coverage too can warn you to phishing emails and ransomware scams, maintaining your individual data and virtual belongings protected. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS device.
2) Double-check websites: All the time check web site addresses and use bookmarks for relied on websites. As an alternative of clicking on hyperlinks in emails or messages, manually kind the URL or use a relied on bookmark. This minimizes the chance of touchdown on a fraudulent web page designed to imitate a valid web site.
3) Replace your gadgets: It’s possible you’ll surprise how maintaining your gadgets up to date is helping towards malware like Astaroth. Whilst it doesn’t immediately save you an assault, it guarantees the placement doesn’t worsen. Keeping your operating system and applications up to date with the most recent safety patches closes vulnerabilities that malware may exploit, making it tougher for attackers to realize a foothold for your instrument.
4) Keep away from typing passwords: Keep away from getting into passwords each time conceivable to cut back the chance of credential robbery. As an alternative, use authentication strategies like passkeys, Google Signal-In or Apple Signal-In.
A passkey is a characteristic that makes use of cryptographic key pairs to make sure your identification, getting rid of the will for standard passwords. It permits you to check in to apps and internet sites the usage of the similar procedure you employ to liberate your instrument, equivalent to biometrics, PIN or trend.
Google Sign-In is a characteristic that permits you to log in to third-party apps or web sites the usage of their Google Account credentials. It simplifies the sign-in procedure via getting rid of the wish to create and take into account separate usernames and passwords for each and every carrier. You’ll be able to check in by the use of a “Check in with Google” button, a Google sign-in urged or automated sign-in if up to now approved.
Apple Signal-In is a characteristic that allows you to privately check in to taking part third-party apps and internet sites the usage of your Apple ID. It provides a quick, simple and extra non-public technique to authenticate with out the wish to create new accounts or take into account further passwords. To arrange an account to “Check in with Apple,” when a taking part web site or app asks you to arrange or improve an account, do the next: Faucet Check in with Apple. Observe the onscreen directions. Some apps (and internet sites) don’t request your title and e mail cope with. On this case, you merely authenticate with Face ID or Contact ID (relying for your fashion), then get started the usage of the app. Others would possibly ask on your title and e mail cope with to arrange a personalised account. When an app asks for this data, Check in with Apple presentations your title and the private e mail cope with out of your Apple Account so that you can evaluation.
Those strategies depend on cryptographic keys or safe tokens, making it a lot tougher for attackers to intercept your login data, despite the fact that they organize to trick you into visiting a malicious web site.
FBI WARNS OF DANGEROUS NEW ‘SMISHING’ SCAM TARGETING YOUR PHONE
Kurt’s key takeaway
Astaroth displays simply how a ways phishing kits have come, taking issues past the standard methods and bypassing 2FA conveniently. It’s a reminder that regardless of how safe we predict our programs are, there’s at all times a wiser assault ready to take advantage of the gaps. Cybercriminals are adapting rapid, and whilst conventional defenses won’t reduce it anymore, there are nonetheless steps you’ll be able to take to combat again: use passwordless logins, keep up to date and continue learning about those evolving threats.
What do you suppose governments and firms will have to be doing to give protection to you from refined cyber threats just like the Astaroth phishing equipment, which will bypass conventional safety features? Tell us via writing us at Cyberguy.com/Contact.
For extra of my tech guidelines and safety signals, subscribe to my unfastened CyberGuy Document Publication via heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Observe Kurt on his social channels:
Solutions to the most-asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.



